Permissions in AutoPatcher
AutoPatcher allows privileged Users to define very granular sets of permissions for themselves, other Users or API keys. For example, you can limit the access to certain resources only, or narrow the permissions down only to some types of actions.
Granting permissions is done by creating roles and then assigning the appropriate User or API key to one or more roles.
Permissions can be browsed and managed in the Permissions view.
Managing Roles
A Role contains a definition of an access to certain resources and operations that can be performed on them.
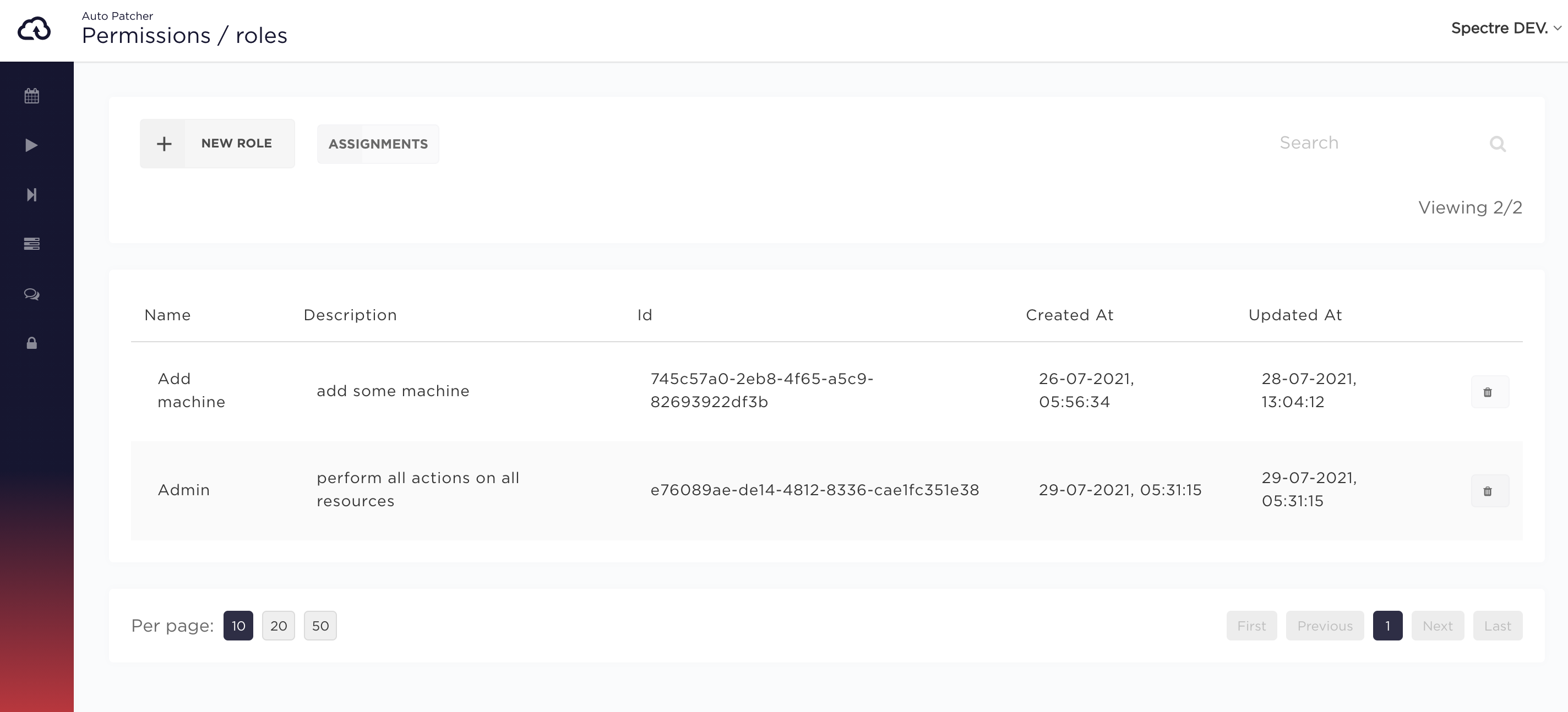
To create a new Role click the New Role button.
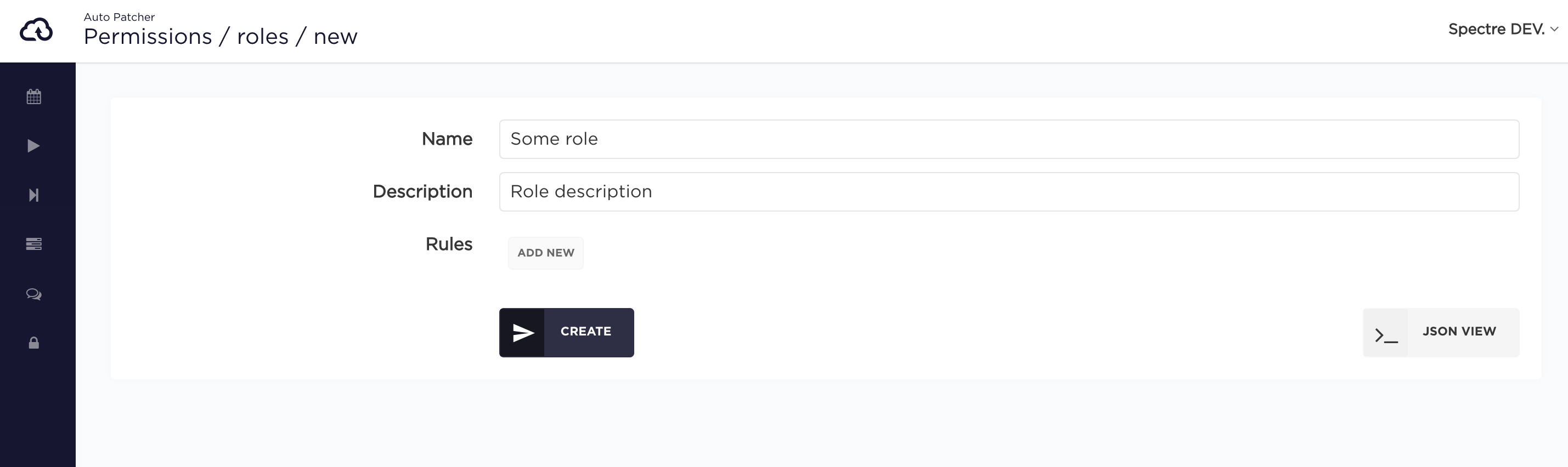
To define permissions within a role, you need to create Rules. A Rule allows to define Resources, Actions and optionally Resource Ids that the Rule will apply to. The Role has all the permissions from all its Rules combined.
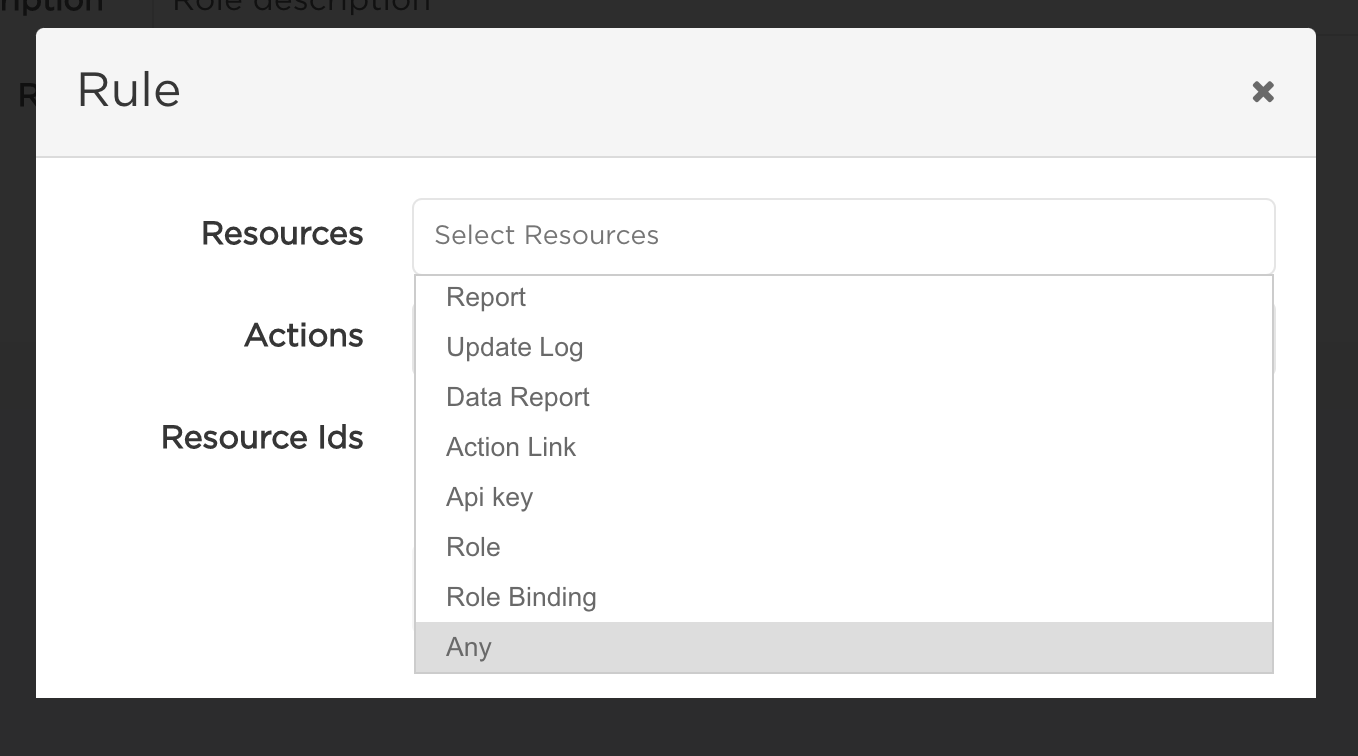
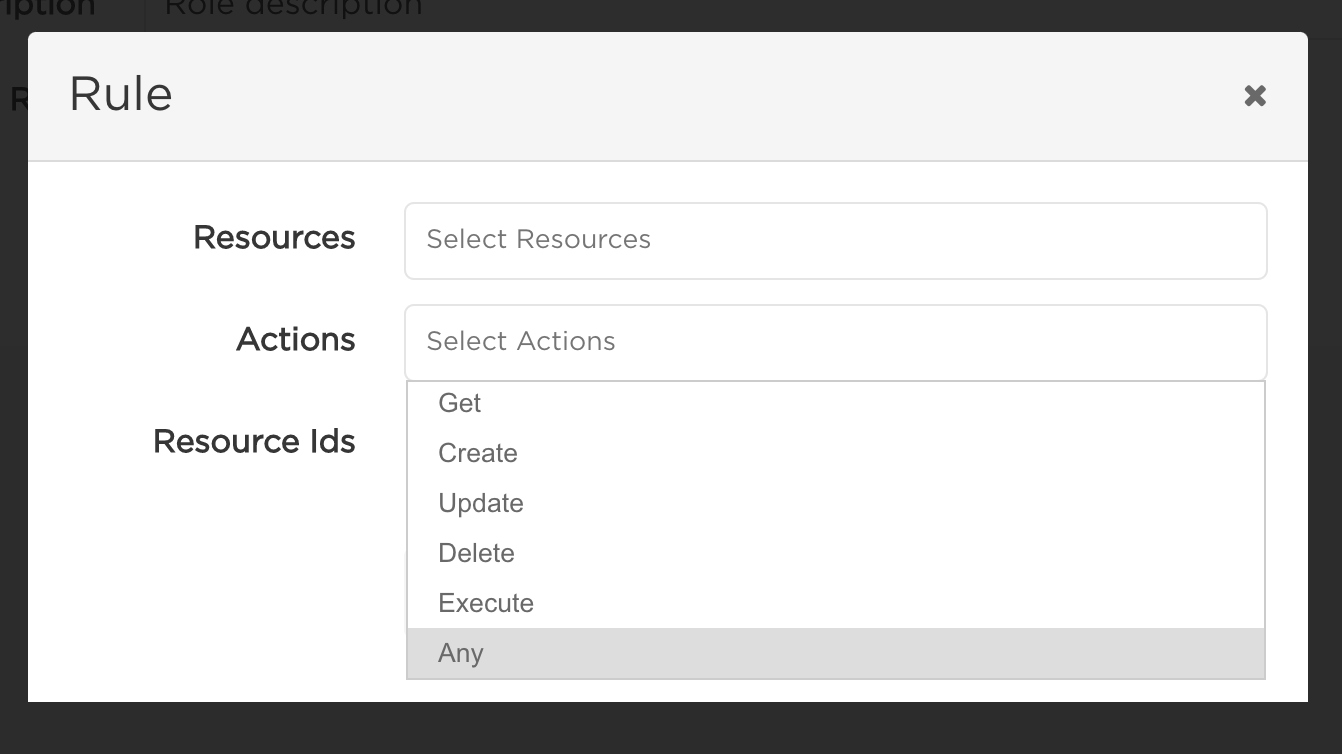
After specifying the Rule (or multiple Rules), click Create to complete.
Resource to action mapping
The following table represents the relations between AutoPatcher resources and the actions which are available for them.
| Resource \ Action | get | list | create | update | delete | execute |
|---|---|---|---|---|---|---|
action_link | ✓ | |||||
activation | ✓ | |||||
api_key | ✓ | ✓ | ✓ | ✓ | ✓ | |
role | ✓ | ✓ | ✓ | ✓ | ✓ | |
role_binding | ✓ | ✓ | ✓ | ✓ | ✓ | |
customer | ✓ | ✓ | ✓ | ✓ | ||
data_report | ✓ | |||||
event | ✓ | ✓ | ✓ | ✓ | ✓ | |
installer_key | ✓ | ✓ | ✓ | |||
machine | ✓ | ✓ | ✓ | ✓ | ✓ | |
notification_group | ✓ | ✓ | ✓ | ✓ | ✓ | |
pipeline | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
plan | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
report | ✓ | |||||
update_log | ✓ | ✓ |
The ✓ in the particular cell of the table means that the action can be performed on the resource,
whereas an empty cell means that the particular resource-to-action mapping has no effect on AutoPatcher's processing.
Example:
- The
listaction for themachineresource is defined, which means that there is a logical use-case for this: retrieving a list of machines. - The
createaction for theupdate_logresource is not defined, since the update log is created automatically as a result of the patching command executed on the machine and this process is not controllable by the user.
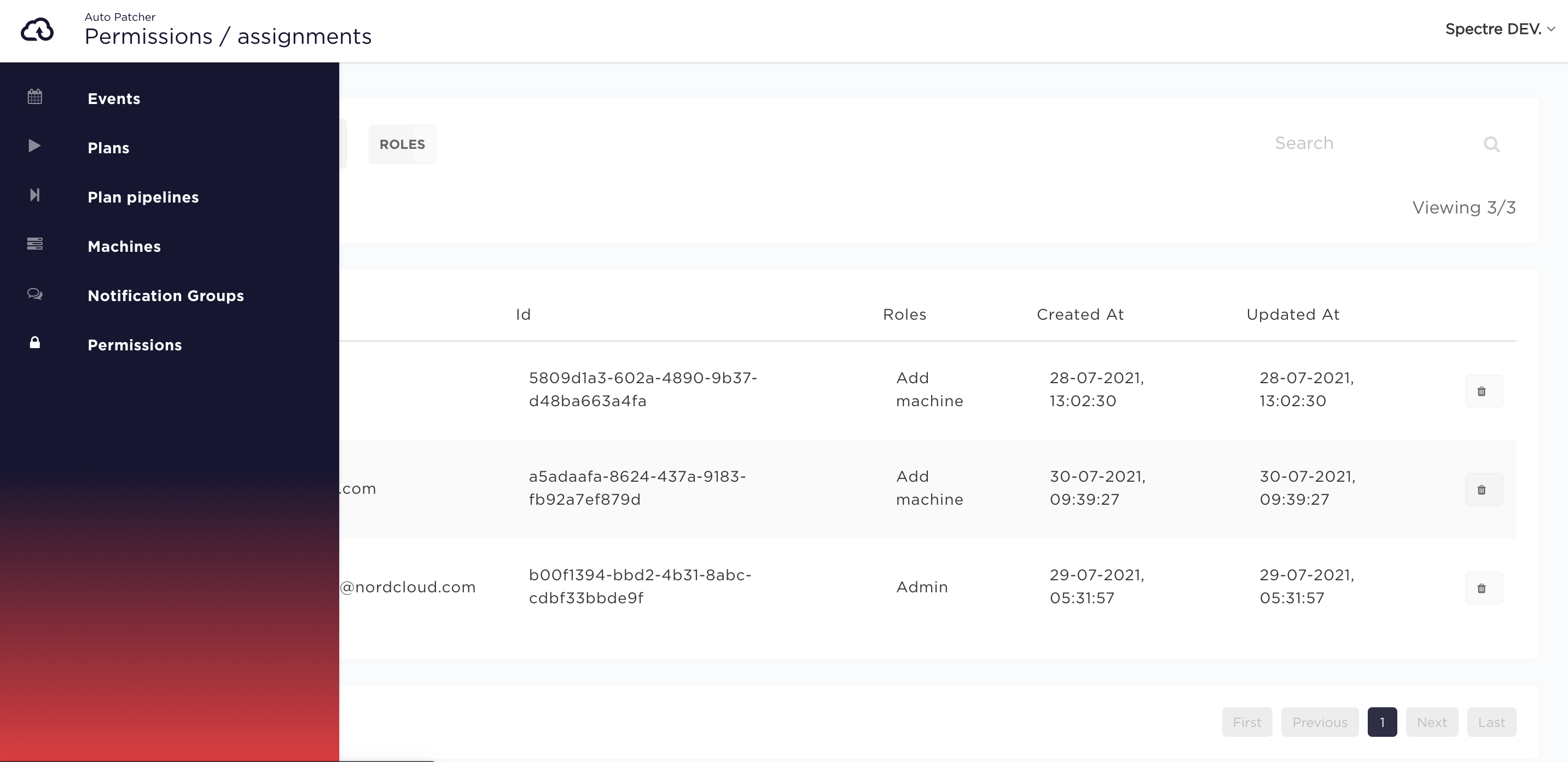
Managing Assignments
Assignments are bindings of Roles to Users or API keys.
In order to create a new Assignment, click 'New Assignment' button.
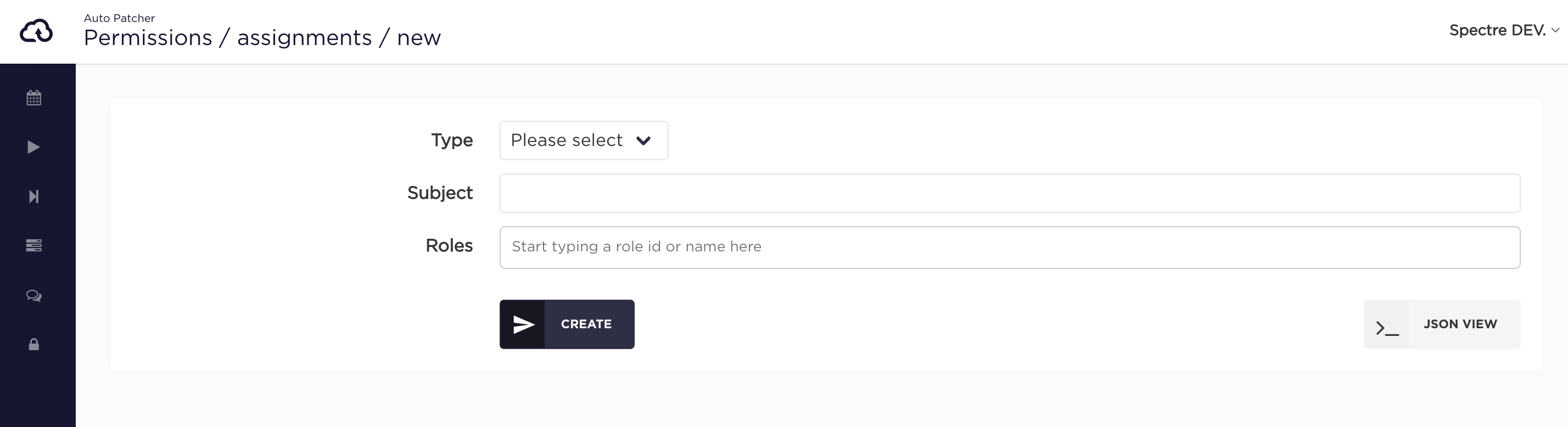
Choose an Assignment type - USER or API_KEY.
- for
USERtype you need to provide email address - for
API_KEYtype you need to provide id of the API key
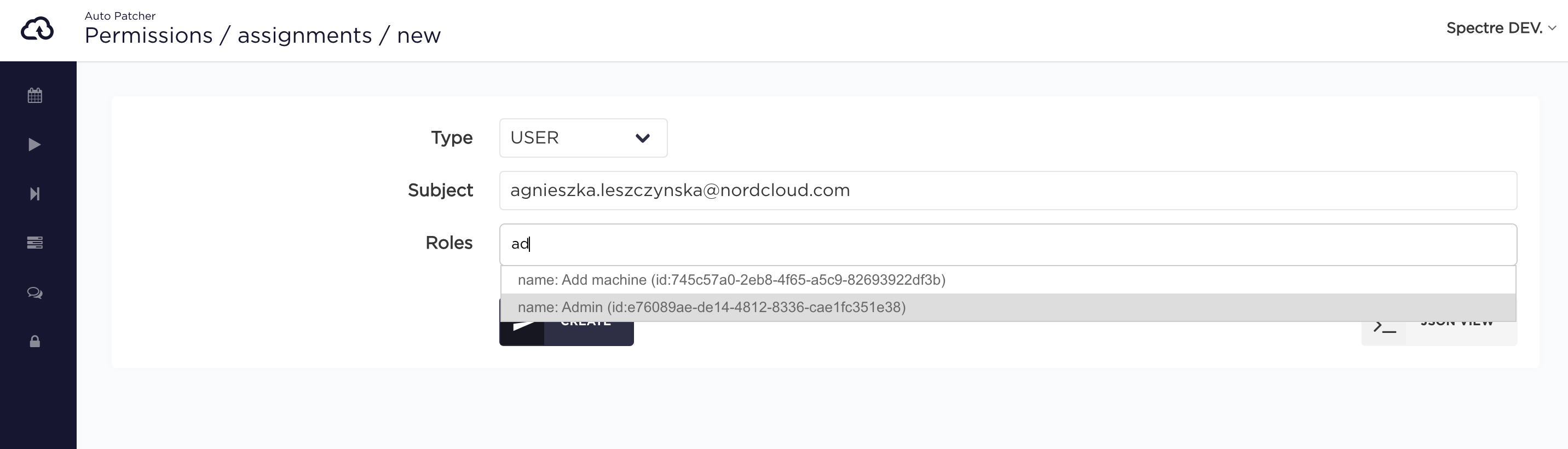
Choose a Role (or multiple Roles) from the ones available. Click 'Create' to complete.
Delay of the permissions changes
The important thing to remember is that the changes in the permissions made by the user don't take effect immediately. Usually, it takes up to 1-2 minutes for the new permissions to apply due to the asynchronous nature of the RBAC rules evaluation.